I have reviewed the most recent news and developments regarding browser extensions from the past seven days (December 21–28, 2025). The industry is currently facing a period of intense volatility, characterized by high-profile security breaches, the final stages of a major architectural shift, and a surge in AI-driven tools. Below is a comprehensive overview of these events and what they mean for the future of the web ecosystem.
- 1. Trust Wallet Incident: Anatomy of the “Christmas Hack” and a Systemic Crisis of Trust
- 2. Threat Landscape 2025: From Hidden Espionage to Browser Ransomware
- 3. Technological Shift: End of the Manifest V2 Era and Transition to Manifest V3
- 4. Browser Security Updates: December 2025 Patch Cycle
- Mozilla Policy: Data Transparency and Community Support
- Extensions of 2025: AI Dominance and New Product Launches
- Perspectives and Conclusions: The Future of the Extension Ecosystem
The final week of December 2025 was marked by unprecedented turbulence in the browser software industry. The period from December 21 to 28 became the culmination of long-term trends, where critical failures in supply chain security collided with the final implementation of new technological standards. While browser developers like Google, Microsoft, and Mozilla sought to strengthen their platforms through the transition to Manifest V3 and the implementation of strict data transparency policies, cybercriminal groups demonstrated high adaptability, exploiting trust in popular extensions with audiences in the millions. This report presents a deep analysis of the current market state, mechanisms of recent attacks, and the future development vector of extensions as a critical element of modern web infrastructure.
1. Trust Wallet Incident: Anatomy of the “Christmas Hack” and a Systemic Crisis of Trust
The most high-profile event of the reporting period was the compromise of the Trust Wallet extension for Google Chrome, which resulted in users losing cryptocurrency assets totaling approximately $7 million. The incident, officially confirmed on December 26, 2025, demonstrated the vulnerability of even the most secure software products to supply chain attacks.

Chronology and Compromise Mechanisms
The investigation showed that the attack was not spontaneous. Preparation began at least two weeks before the active phase. Attackers registered the control domain metrics-trustwallet.com on December 8, 2025, via the registrar NICENIC INTERNATIONAL. This domain was specifically chosen to mimic a legitimate metric collection service. The first requests to the data exfiltration server were recorded on December 21, indicating preliminary testing of the attackers’ infrastructure.
| Date and Time (UTC) | Event | Description |
| 08.12.2025 02:28 | C2 Domain Registration | Infrastructure creation at metrics-trustwallet.com. |
| 21.12.2025 | Start of Network Activity | First requests to api.metrics-trustwallet.com. |
| 24.12.2025 12:32 | Version 2.68 Publication | Malicious code injected into the Chrome Web Store. |
| 26.12.2025 11:00 | Public Admission | Official Trust Wallet statement on the incident. |
| 26.12.2025 | Version 2.69 Release | Cleaned update available for users. |
The attack mechanism was based on injecting malicious code directly into the application’s analytics logic. The attackers used the legitimate open-source library posthog-js to mask data theft as regular telemetry traffic. The malicious script iterated through all wallets stored in the extension and initiated a request for the mnemonic phrase (seed phrase). When a user entered their password to unlock the wallet, the extension decrypted the phrase and sent it in plain text to the attackers’ server inside the errorMessage field.
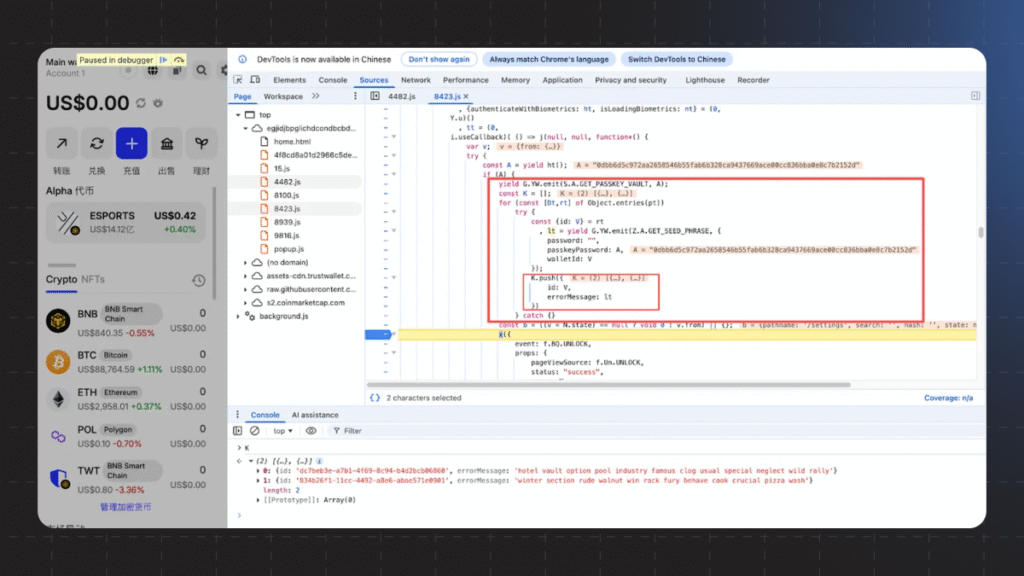
API Key Leak and Bypassing Verification Systems
The key factor that allowed an attack of this scale was the leak of a Chrome Web Store API key belonging to the Trust Wallet development team. According to Trust Wallet CEO Eowyn Chen, this allowed the attackers to bypass standard manual release checks and internal code audit procedures, publishing malicious version 2.68 directly to the marketplace. This event underscores that extension security in 2025 depends not only on code quality but also on strict hygiene in managing credentials and secrets during the development process.
Analysis of the stolen assets indicates a professional level of attackers (APT-level). As of December 26, the losses were distributed as follows:
- Bitcoin (BTC) network: approximately 33 BTC (approx. $3 million).
- Ethereum (ETH) and Layer-2 solutions: over $3 million.
- Solana (SOL) network: approximately $431.
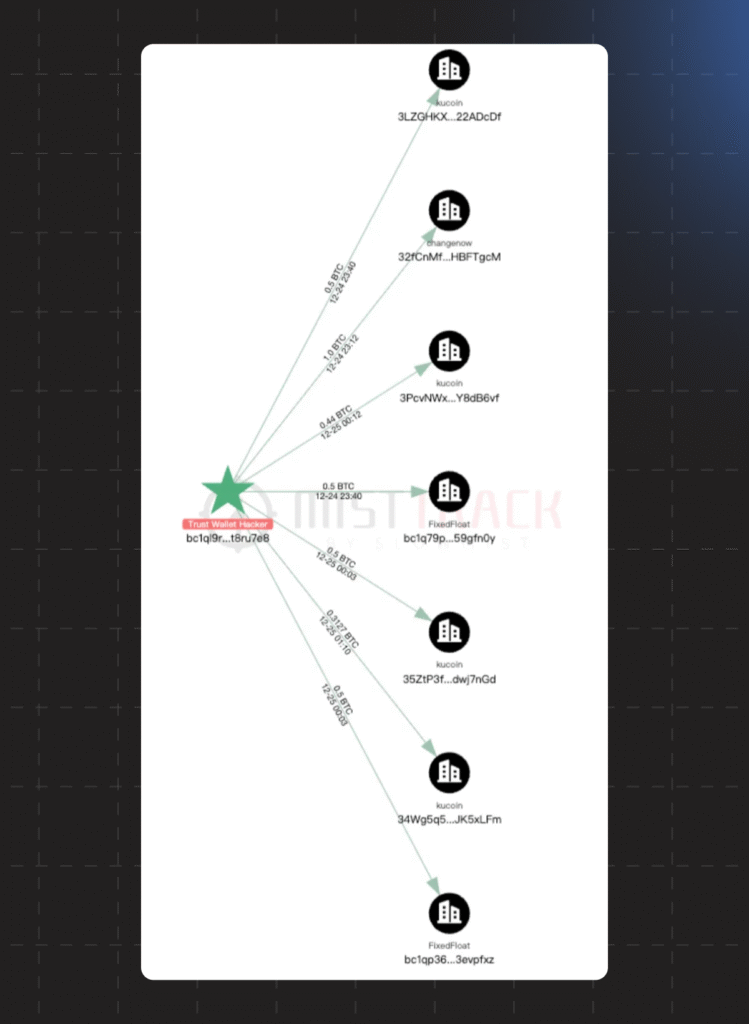
The funds were laundered through automated exchange services such as ChangeNOW and FixedFloat, as well as the KuCoin exchange, complicating further tracking. The incident only affected Chrome extension users; mobile versions and extensions for other browsers remained secure.
2. Threat Landscape 2025: From Hidden Espionage to Browser Ransomware
Beyond the catastrophic Trust Wallet hack, December 2025 revealed a series of other long-term threats transforming the understanding of risks when using browser add-ons. Extensions have ceased to be simple auxiliary tools and have evolved into full-fledged platforms for cyber espionage and data exfiltration.
ShadyPanda Campaign: Seven Years of Invisible Control
In mid-December, security researchers uncovered the activities of the ShadyPanda group, which had quietly hijacked popular Chrome and Edge extensions on a massive scale for seven years. The campaign affected over 4.3 million users. Attackers purchased or hacked developer accounts of legitimate extensions and pushed malicious updates that gradually turned the add-ons into Remote Code Execution (RCE) frameworks.
Key capabilities of compromised ShadyPanda extensions included:
- Full-scale Monitoring: Collecting every visited URL and logging keystrokes.
- SaaS Session Manipulation: Intercepting session tokens for platforms like Microsoft 365 and Google Workspace, allowing attackers to bypass multi-factor authentication and access corporate data.
- Dynamic JavaScript Execution: The ability to download and run arbitrary code within the context of any webpage, making the extensions ideal tools for phishing and script injection.
Since extension updates happen automatically and invisibly to the user, a trusted tool could become malicious “overnight”. This raises questions about the need for more transparent user notification mechanisms regarding changes in code and extension permissions.
Urban VPN and Exploitation of AI Interest
Another example of unethical extension behavior was the activity of Urban VPN. By December 15, 2025, it was revealed that version 5.5.0 of this popular VPN service began secretly collecting data from AI chats (ChatGPT, Claude, Gemini). The extension intercepted user prompts and AI responses, including session metadata, and sent them to Urban VPN servers for subsequent resale to data brokers and advertisers.
Adding to the cynicism, the extension included an “AI Protection” feature that supposedly warned users about the risks of transferring data to AI companies. In reality, data collection occurred regardless of whether this “protection” was enabled. By December 23, the extension was removed from all major stores (Chrome Web Store and Microsoft Edge Add-ons), but millions of users who had already installed it remained at risk until manual removal.
New Vectors: Syncjacking and Browser Ransomware
December 2025 research also points to more sophisticated attack methods, such as Browser Syncjacking. This method allows attackers to use extensions with simple read/write permissions (e.g., grammar checkers like Grammarly) to take control of an entire device via the Google Workspace profile sync feature.8 An attacker can replace legitimate update files (e.g., for Zoom) with malicious executables using the extension as an intermediary.
Furthermore, the emergence of “browser-native ransomware” has been recorded. Unlike traditional ransomware, these attacks do not require local files. Given that in 2025, over 80% of corporate data is stored in the cloud, attackers use extensions to systematically exfiltrate data from SaaS applications and subsequently demand a ransom, bypassing traditional antivirus and EDR systems.
3. Technological Shift: End of the Manifest V2 Era and Transition to Manifest V3
The last week of December 2025 was a period of final summation for the transition of Chromium-based browsers to the Manifest V3 (MV3) platform. This process, initiated by Google back in 2021, entered its final phase of blocking legacy extensions in December 2025.
Deprecation Status and User Impact
For most Chrome users, the transition was painful. Manifest V2 (MV2) based extensions, including the classic uBlock Origin, were finally disabled in stable browser versions (version 138 and higher). Users began receiving notifications that their favorite add-ons were “no longer supported,” sparking a wave of criticism on social media and forums.
| User Category | MV2 Support Status (Dec. 2025) | Comment |
| Regular Chrome Users | Fully Disabled | Transition to MV3 alternatives required. |
| Enterprise Clients (Managed) | Supported until June 2025 | Via ExtensionManifestV2Availability policy. |
| Firefox Users | Supported | Mozilla maintains MV2 support for flexibility. |
| Edge/Brave Users | Partial/Limited | Transition driven by the Chromium engine. |
The Ad-Blocking Conflict
The main point of contention in the MV3 transition was the restriction of the webRequest API, which allowed ad blockers to dynamically modify network requests. In the new architecture, developers are required to use the declarativeNetRequest API, where filtering logic is passed to the browser as static rules. Critics argue this change primarily benefits Google’s advertising business by reducing the effectiveness of complex blocking algorithms.
While developers like AdGuard and Ghostery released MV3-compatible versions, they admit the functionality of these extensions (e.g., uBlock Origin Lite) is limited compared to MV2 versions. In response, a notable migration of privacy-oriented users toward the Firefox browser has been observed, as it not only implemented MV3 support but also maintained MV2 compatibility and provided extended API support for blockers.
4. Browser Security Updates: December 2025 Patch Cycle
In response to growing threats, browser developers synchronously released critical updates in mid and late December. These patches aimed to address zero-day vulnerabilities actively used in targeted attacks against high-profile individuals and corporate employees.
Google Chrome 143: Closing 21 Vulnerabilities
On December 18, 2025, Google released Chrome update 143.0.7499.169 for Windows, Mac, and Linux. This release became one of the most significant for security in Q4 2025, fixing 21 vulnerabilities of various severity levels.
Key fixes included:
- CVE-2025-13630: A typical 2025 type confusion error in the V8 JavaScript engine, potentially allowing Remote Code Execution (RCE).
- CVE-2025-14174: An out-of-bounds memory access error in the ANGLE library (Metal renderer), discovered by Google TAG and Apple SEAR. This vulnerability was actively exploited “in the wild”.
- CVE-2025-14765: A use-after-free vulnerability that could lead to heap corruption upon visiting a specially crafted malicious webpage.
Microsoft Edge and Safari: Combatting WebKit Exploitation
Microsoft released Edge 143.0.3650.96 also on December 18, incorporating Chromium project fixes and browser-specific patches. A major new feature was the ability to detect and automatically revoke malicious sideloaded extensions, a response to the rise in attacks through malicious software installers.
Apple, for its part, introduced Safari 26.2 and updates for all its OS versions (iOS 26, macOS Sequoia) to close two critical vulnerabilities in the WebKit engine (CVE-2025-43529 and CVE-2025-14174) used in “extremely sophisticated attacks against specific individuals”. The fact that the same vulnerabilities affect both Chrome (via ANGLE) and Safari (via WebKit) points to the deep interconnectedness of modern browser technologies.
Mozilla Policy: Data Transparency and Community Support
Amid Google’s strict measures, Mozilla chose a “soft power” path, focusing on transparency and encouraging quality development.
New Data Collection Disclosure Standards
Starting November 3, 2025, Mozilla introduced a mandatory requirement for all new Firefox extensions: declaring data collection policies directly in the manifest.json configuration file via the data_collection_permissions key. This allows users to see exactly what data an extension collects even before installation.
- If an extension does not collect data, the developer must explicitly state so (value
none required). - If a declaration is missing or false, the extension is blocked from the AMO store.20This initiative aims to combat “hidden espionage,” like the Urban VPN case, and makes Firefox a leader in verifiable disclosure of data practices.
2025 Firefox Extension Developer Awards
On December 17, 2025, Mozilla announced the winners of its extension developer awards, recognizing the contributions of over 10,000 creators.
| Award | Extension | Why it Matters |
| Platinum | uBlock Origin | Recognized for surpassing 10.5 million users and commitment to privacy. |
| Silver | Privacy Badger | An EFF product that became a standard for fighting unwanted tracking. |
| Silver | AdGuard | Noted for an effective combination of ad blocking and protection from malicious sites. |
| Bronze | Bitwarden | Leader among open-source password managers. |
| Bronze | ClearURLs | Small but important tool for cleaning tracking parameters from URLs. |
These awards serve as a guide for users, helping them choose verified and secure tools amidst a growing number of malicious imitations in stores.
Extensions of 2025: AI Dominance and New Product Launches
In 2025, browser extensions finalized their transformation from simple utilities to proactive AI assistants. December reports from Google and new releases on Product Hunt confirm this trend.
AI as an “Always-On” Companion
Google highlighted the best extensions of 2025, with AI copilots taking leading positions. Tools like Monica and Sider have become the standard for content work: they allow users to summarize long webpages, rewrite emails, and “chat” with PDFs without switching tabs.23
Other significant AI tools of December 2025:
- HARPA AI: An extension combining web automation (price monitoring, data tracking) with generative AI.
- Fireflies.ai and Bluedot: Meeting intelligence tools that automatically record, transcribe, and create summaries of virtual meetings.
- Phia: A personal shopping assistant that finds the best prices and deals in real-time while browsing products.
Perspectives and Conclusions: The Future of the Extension Ecosystem
The events of the last week of December 2025 allow for several fundamental conclusions about where the industry is heading.
- Security through Architecture: The transition to Manifest V3, despite community criticism, is a necessary step to limit the rights of malicious extensions. However, the Trust Wallet example shows that architectural limitations are powerless against the theft of developer API keys. The future of extension security lies in combining MV3 with stricter developer authentication methods (e.g., hardware keys for Store publishing).
- AI as a Double-Edged Sword: We see that AI is a powerful productivity tool (Monica, Sider), but it also becomes a target for attackers. The theft of AI prompts (Urban VPN) will become one of the main vectors of cyber espionage in 2026, as prompts often contain trade secrets.
- Edge AI (Local Computing): Mozilla’s initiative to introduce ML APIs in Firefox opens the door to “private” automation. If machine learning tasks are performed locally in the browser rather than in the cloud, it will eliminate much of the privacy risk associated with the current generation of AI extensions.
- Browser Market Fragmentation: Differences in approach to extension support between Chrome and Firefox could lead to a redistribution of market share. If Chrome continues to aggressively limit customization under the guise of security, Firefox will strengthen its position as the “browser for power users and privacy advocates.”
In summary, 2025 concludes with the recognition of the browser extension as a critical yet highly vulnerable link in digital security. Users and organizations are recommended to adopt a “minimum necessary extensions” policy, regularly audit installed add-ons, and favor tools recognized for security and transparency. In an environment where the browser is becoming the primary work environment (OS-in-a-browser), control over extensions is equivalent to control over the entire information system.